How Can I Repair A Hacker Lockout On Hp Laptop
When I have started to larn
Today I can understand your condition if you are learning how to hack and yet confused about hacking tools used past pro hacker and penetration tester then this post is relevant for you lot.
Free Hacking tools for Information Gathering
#1 OSINT Framework
OSINT Framework This is non a tool only framework focused on gathering information using unlike tools bachelor open up source (over net). The intention is to help people find gratuitous OSINT resources. Some of the sites included might require registration or offer more than data for $$$, but yous should be able to go at least a portion of the bachelor information for no cost.
#ii SHODAN
SHODAN: Shodan likewise is not a tool, it is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) continued to the net using a variety of filters. Some have as well described information technology as a search engine of service banners, which are metadata that the server sends back to the client.[ane] This can exist information about the server software, what options the service supports, a welcome message or anything else that the client can discover out before interacting with the server.
#3 Check User Name
CheckUserName: Information technology is an online service that helps hacker to cheque usernames more than over 170 social networks. This is specially useful if Hacker is looking for social media accounts with a specific username and helpful The penetration tester for running an investigation to decide the usage of the same username on different social networks.
#4 Google Dorks
#5 Maltego
Maltego: Maltego is the passive information gathering tool condition if
Maltego Kali Linux Tutorial
#6 Recon-ng
Recon-ng: Recon-ng is some other corking tool pre-congenital in Kali Linux used to perform gathering information chop-chop. information technology is a full-featured Web Framework, information technology's written in python. Consummate with independent modules, database interaction, built-in convenience functions, interactive assistance, and command completion, Recon-ng provides a powerful environs in which open up source web-based reconnaissance can be conducted speedily and thoroughly.

#7 Whois
A whois Kali Linux command is a utility as a role of the information gathering used in all of the Linux-based operating systems. this tool is part of information security cess, and ane of the information gathering techniques. there are a lot of information gathering strategies. It is used to identify domain information and more. Whois.com
#8 DIG (Domain Data Gropper)
Dig: The 'dig command' is used in network administration that check and lookup domain name server (DNS) It is dnssec and the office of information gathering.
dnsenum
Find Information related Domain Name servers, mail service servers, commutation server, file server etc.
#9 Theharvester
Theharvester: Take hold of email addresses by using information technology search engine database, it is mostly used to collect email details of particular domain. thehaverster in Kali Linux tutorial

#ten Creepy
Creepy: Creepy is a geolocation OSINT tool for penetration tester. Gathers geolocation related information from online sources past querying social networking platforms like Twitter, Flicker, and Facebook etc, and allows for presentation on map.
If anyone uploads images on social media with geolocation activated then you lot volition come across a total
It search filtering based on exact location and/or date, export in csv format or kml for further assay in Google Maps.

Free Hacking tools for Network Scanning
#11 Nmap – A Network Scanner Free tool

Nmap is a free hacking tool and near used worldwide in terms of network scanning. It is used to notice live hosts in the network, open up ports of devices, running service on the aforementioned port with version detail, besides used for vulnerability scanning.
It is free tool and bachelor for windows, Linux, Costless BSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more.
Nmap is a powerful tool, has been used to scan huge networks of literally hundreds of thousands of machines in the same network or the network

Some Important Tutorials Hither
- Kali Linux Scan Network by
nmap pingsweep – [Total Guide] - eight important
nmap commands in Kali Linux with Instance - vii Techniques of Nmap port scanner – Scanning
- five Nmap Timing Templates – You should know
- How to save Nmap output to file Case
- v examples of Nmap Scripts in Kali Linux
#12 Angry IP Scanner

Aroused IP Scanner is an open-source, simple and fast tool to use. It is a cross-platform network scanner.
It is widely used by network administrators, hackers, Penetration tester and just curious users around the world, including big and minor enterprises, banks, and government agencies.
It is available for Linux, Windows, and Mac Bone X, may be supporting other platforms as well.
It scans IP addresses and ports also every bit has many other features as below:
- Scans local networks equally well as Interne
- IP Range, Random or file in any format
- Exports results into many formats
- Extensible with many data fetchers
- Provides control-line interface
- Over 29 million downloads
- Free and open-source
- Works on Windows, Mac and Linux
- Installation not required
#13 Advanced IP Scanner

It provides remote control over computers using RDP and Radmin, and can even switch off computers.
It is available in a portable fashion, you can have this tool in your pen bulldoze.
#fourteen IP Scanner
It is
Features are:
- browse IP ranges automatically or on demand
- re-observe an unabridged subnet with merely one click
- exclude devices from the results based on type or IP address
- import your entire network setup via a CSV file
- and exercise then much more than!
#fifteen Hping3
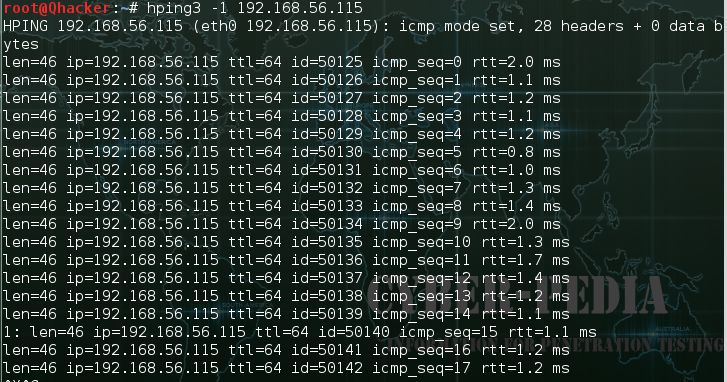
It is available in Kali Linux by default it is one of DOS attack software, DDOS represent distributed deprival of service attack. you can launch and end the DOS attack, whenever yous want. In this analogy, hping3 volition act as an ordinary ping utility, sending ICMP-reverberation und getting ICMP-answer
Tutorial Commodity: 10 hping3 examples for scanning network in Kali Linux
#16 NetDiscover
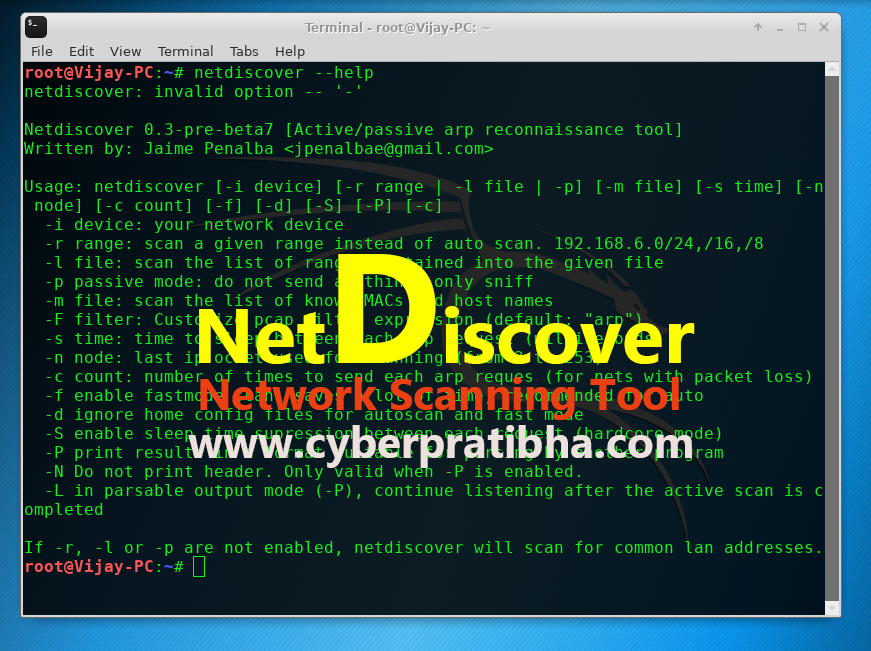
Netdiscover is an ultimate scanning tool used to become the internal IP address and MAC address of alive hosts in the network. Netdiscover is a pre-installed tool in Kali Linux, if you are using Kali Linux and so you don't need to install
Must Read: 10 best open port checker Or Scanner
Vulnerability Assesment tools
#17 OpenVAS

OpenVAS does not default in Kali Linux if you desire to use, you must install information technology beginning. It is available on the Kali Linux repository so you tin install directly from the final using apt-go utility.
OpenVAS Documentation
The OpenVAS scanner is a comprehensive vulnerability assessment organisation that tin can detect security problems in all manner of servers and network devices.
Results will be delivered to your email address for assay; allowing yous to first re-mediating any risks your systems confront from external threats.
Vulnerability scanning is a crucial phase of a penetration test and having an updated vulnerability scanner in your security toolkit can often brand a real difference by helping you notice overlooked vulnerable items. For this reason, we've manually packaged the latest and newly released OpenVAS 8.0 tool and libraries for Kali Linux. Although nothing major has inverse in this release in terms of running the vulnerability scanner, we wanted to give a quick overview on how to get information technology up and running.
#19 Nikto – Web Scanner
Nikto is
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific issues on over 270 servers. It as well checks for server configuration items such as the presence of multiple alphabetize files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can exist automatically updated.
Run into All features of Nikto: https://cirt.net/Nikto2
Nikto Tutorial:
#20 Nexpose – Community Improver
Nexpose community vulnerability tool is developed by Rapid7 which is an open source tool. Information technology is widely used for vulnerability scanning and a wide range of network intrusion checks. The following are the central features of Nexpose Customs tool.
- The tool is quite detailed in its scanning where it takes into business relationship the historic period of the vulnerability such as malware kit employed, the advantages taken by the kit, etc.
- The tool can be hands combined with a Metaspoilt framework.
- The tool is capable to scan the new devices in order to find the vulnerabilities and evaluate the network.
- It tin monitor the vulnerabilities exposures real fourth dimension and can familiarize itself to the latest hazards very efficiently.
- The tool categorizes the risks post scanning for vulnerability into low, medium, or high scale.
Download Nexpose: Nexpose Comunity Adition
#21 Retina CS Community
Retina CS is an open source free vulnerability scanner tool. It is a spider web-based console. Information technology is used
Features:
- The tool is skillful for network security administrators, assist to saves both time and coin required for network security management.
- It can perform automatic vulnerability scans for workstations, web servers, web applications, and databases very swiftly.
- It tin can provide an assessment of cross-platform vulnerability.
- Information technology has features to provide patching, configuration compliance, compliance reporting, etc.
- The tool supports virtual environments such every bit virtual app scanning, vCenter integration, etc.
Download: Retina CS Community Tool
Web Awarding Analyzing Tools
#22 WPscan
Wpscan a small tool written in scarlet and preinstalled in Kali Linux, if you are using another Linux distribution, and so install wpscan first.
Wpscan is used to scan the
WPscan Tutorial: WpScan
#23 HTTrack – Website Copier
HTTrack is a free (GPL, libre/gratis software) and like shooting fish in a barrel-to-use offline browser utility.
It allows you to download a Www site from the Cyberspace to a local directory, edifice recursively all directories, getting HTML, images, and other files from the server to your computer. HTTrack arranges the original site's relative link-structure. Simply open a page of the "mirrored" website in your browser, and you tin can browse the site from link to link, equally if you were viewing it online. HTTrack can also update an existing mirrored site, and resume interrupted downloads. HTTrack is fully configurable, and has an integrated help arrangement.
WinHTTrack is the Windows (from Windows 2000 to Windows x and above) release of HTTrack, and WebHTTrack the Linux/Unix/BSD release.
See the download folio. HTTrack Download
How to employ
How to utilise
#24 Arachani Web Scanner

If you are Kali Linux user, then y'all shouldn't worry about arachani web scanner is available for Kali Linux. Just run following command to install
#apt-become install arachni
The Arachni scanner is an escalated tool that runs from a spider web interface much likened to that of Tenable'due south Nessus. Notwithstanding, dissimilar to Nessus, Arachni can just perform a scan confronting one host on 1 port at a time. On the off gamble that in that location are different web services running on a host and non serviced from the port, so repeated scan volition
Tutorial : How to use Arachni scanner for Web Application vulnerability in Kali Linux
#25 sqlmap – Database Enumerator
Sqlmap is default in Kali Linux, Use and enjoy to get of import information from database server.
sqlmap is an open source penetration testing tool that automates the procedure of detecting and exploiting SQL injection flaws and taking over of database servers.
It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over information fetching from the database, to accessing the underlying file system and executing commands on the operating organization via out-of-ring connections.
Features :
- Supported databases are MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, HSQLDB.
- Six sql injetion techniques support: boolean-based blind, time-based bullheaded, mistake-based, UNION query-based, stacked queries and out-of-band.
- Directly connect to the database and enumerate information without DBMS credentials.
- Information technology can dump databse tables.
- It support to download and upload whatsoever file from the database server underlying file system when the database software is MySQL, PostgreSQL or Microsoft SQL Server.
- the database server underlying file organisation when the database software is MySQL, PostgreSQL or Microsoft SQL Server.
Free Hacking tools for Password Bang-up
#26 John The Ripper

John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS.
John, better known as John the Ripper, is a tool to observe weak passwords of users in a server. John can map a dictionary or some search pattern too as a password file to cheque for passwords. John supports dissimilar bully modes and understands many ciphertext formats, like several DES variants, MD5 and blowfish. It can as well be used to excerpt AFS and Windows NT passwords.
Documentation : https://www.openwall.com/john/physician/
#27 Hashcat
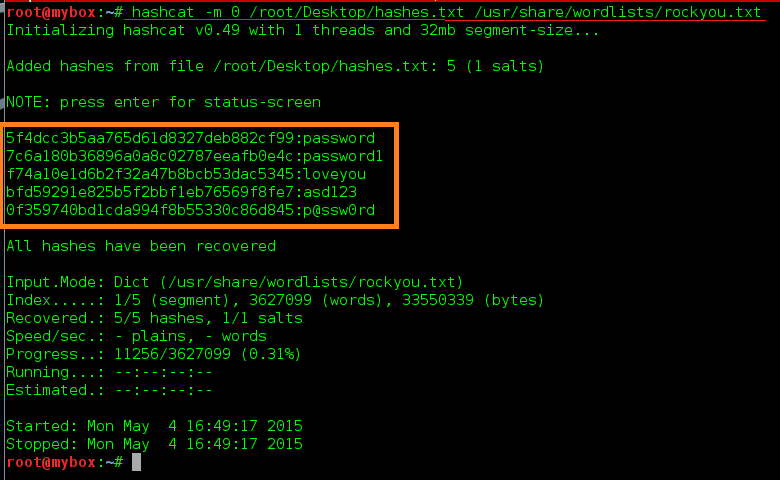
According to official website Hashcat is the earth's fastest CPU-based password recovery tool.
While information technology'south not as fast as its GPU counterpart oclHashcat, big lists can exist hands split in half with a good dictionary and a bit of knowledge of the command switches.
Hashcat was written somewhere in the middle of 2009. Aye, there were already close-to-perfect working tools supporting dominion-based attacks like "PasswordsPro", "John The Ripper". Nonetheless for some unknown reason, both of them did not support multi-threading. That was the only reason to write Hashcat: To make use of the multiple cores of modern CPUs.
Granted, that was not 100% correct. John the Ripper already supported MPI using a patch, merely at that time it worked only for
Must Read: Hashcat Tutorial – Bruteforce Mask Assail
#28 Cain and Abel
Cain & Abel is a password recovery tool for Microsoft Operating Systems. Information technology allows easy recovery of various kind of passwords past sniffing the network, cracking encrypted passwords using Lexicon, Beast-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
Cain and Able Tutorial:
- Most used Password bully techniques past Cain and Abel
- Rainbow Tables Attack (Cryptanalysis attack) and winrtgen
- Cain and Abel software for cracking hashes tutorial
- Dictionary attack For Slap-up passwords using Cain and Abel
- Creature Forcefulness Attack for Neat Passwords using Cain and Abel
#29 Hydra-THC
According to official website of thc-hydra, One of the biggest security holes are passwords, equally every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system and different online services
There are already several login hacking tools bachelor, however the online services Either back up more than than 1 protocol to attack or support panellized Connects.
THC-Hydra Tutorial: Dictionary attack tool thc-hydra tutorial for beginner
#30 FcrackZip
fcrackzip searches each zipfile given for encrypted files and tries to guess the countersign. All files must exist encrypted with the aforementioned password, the more files you provide, the amend.
Have you ever mis-typed a countersign for unzip? Unzip reacted pretty fast with ´wrong password´, without decrypting the whole file. While the encryption algorithm used by zip is relatively secure, PK made cracking like shooting fish in a barrel by providing hooks for very fast password-checking, directly in the zip file. Understanding these is crucial to cipher countersign cracking.
Tutorial: Fcrackzip Windows to crack zero password [Tutorial]
Must Read: Elevation 10 Password cracker software for Windows ten
Free hacking tools for Wi-Fi
#31 Aircrack-ng
Aircrack-ng is not a tool, simply it is a complete prepare of tools including used to audit wireless network security.
It focuses on dissimilar areas of WiFi security:
- Monitoring: Bundle capture and export of data to text files for further processing past third party tools
- Attacking: Replay attacks, deauthentication, imitation access points and others via packet injection
- Testing: Checking WiFi cards and driver capabilities (capture and injection)
- Bang-up: WEP and WPA PSK (WPA 1 and 2)
All tools are command line which allows for heavy scripting. A lot of GUIs have taken advantage of this feature. It works primarily Linux but as well Windows, OS 10, FreeBSD, OpenBSD, NetBSD, as well as Solaris and even eComStation 2
Aircrack-ng Documentation: https://world wide web.aircrack-ng.org/doku.php#documentation
#32 Fern Wifi Cracker
Fern Wifi Cracker is GUI (Graphical User Interface) based tool. It is easy to utilize. If you are not command lover person then this is a best tool for you to crack wifi including WEP/WPA/WPA2.
Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the Python Qt GUI library, the programme is able to fissure and recover WEP/WPA/WPS keys and as well run other
Features:
- WEP Dandy with Fragmentation,Apace, Caffe-Latte, Hirte, ARP Request Replay or WPS assault
- WPA/WPA2 Not bad with Dictionary or WPS based attacks
- Automated saving of central in database on successful scissure
- Automatic Access Point Attack System
- Session Hijacking (Passive and Ethernet Modes)
- Access Bespeak MAC Address Geo Location Tracking
- Internal MITM Engine
- Bruteforce Attacks (HTTP,HTTPS,TELNET,FTP)
- Update Support
Best Tutorial : Fern WiFi Countersign Auditing Tool
#33 Fluxion
Fluxion is a wifi Security analysis tool security study
Complete Tutorial: Fluxion – WPA WPA2 hacking in minutes [2019]
- Hacking wifi countersign in android phone
- 5 Tips, how to secure wifi from hacking – total guide
- five Means to show my saved wifi password in Windows 10
- Top 5 Wifi Hacking software for Linux Bone
Exploitation Tools
#34 Metasploit Framework
If y'all are planning to learn hacking, you lot must learn how to apply metasploit framework.
Metasploit is as important as milk for body.
It is the collection of small tool or scripts used for scanning, enumeration, vulnerability scanning, exploitation, password corking, maintaining access and more.
Yous can say ane framework collection of tool
Metasploit framework Version v5.0.2-dev has
- 1852 exploits
- 1046 auxiliary
- 325 post
- 541 payloads
- 44 encoders
- 10 nops
- two evasion
Metasploit is easy to learn and employ for Hacking or penetration testing. Command line interface makes it more potent and powerful.
You lot can write your ain exploits and utilize within metasploit. It is absolutely Complimentary.
Metasploit Tutorial Links:
- 6 Metasploit Modules – Yous should know
- MSFvenom replacement of MSFpayload and msfencode – Full guide
- 6 Techniques to clarify the vulnerability scan report in Metasploit
- How to use Metasploit for vulnerability scanning
- How to use metasploit pro in Kali Linux
- Creating Persistent Backdoor By Metasploit in Kali Linux
- Creating Trojan Horse (Encoded)Past Using Msfpayload
#35 Armitage
Do Easy and fast hacking with Armitage It is graphical interface of Metasploit framework. It has user friendly interface. Everything in one click.
One click for scanning network.
One Click for run vulnerability scanning, possibilities of exploitation those weakness.
Ane Click for creating backstairs and more than.
Actually information technology is very awesome exploitation framework you must try and use it.
Armitage Tutorial: Transmission Page
#36 Beef – Exploit Browser
BeEF is brusk for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the spider web browser.
Amid growing concerns about web-borne attacks against clients, including mobile clients, Beefiness allows the professional penetration tester to assess the actual security posture of a target environment by using customer-side attack vectors. Unlike other security frameworks, Beef looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the spider web browser.
BeEF volition hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks confronting the arrangement from within the browser context.
#37 Set – Social Engineering Toolkit
It is fourth dimension to exploit man, Yes man can be exploited through the computer. But send a link to him/her, He/she will give you personal data (some time username and countersign) try information technology now.
This is menu based exploitation framework, It means cull the pick from given menu, cull once more and again. Hurrrr y'all launched attack.
It is very usefull for hacking social media accounts like Facebook, twitter, LinkedIn etc.
Do you desire hack Gmail account use it.
https://www.facebook.com/cyrageofficial/videos/980350762138342/
Tutorial Web log
#38 Macchanger
macchanger is a GNU/Linux utility for viewing/manipulating the MAC address for network interfaces.
MAC address is a concrete address of NIC (Network Interface Carte).
Every device in the network has two type of address, One is IP address another MAC address. IP address can be changed easily, only MAC accost can't.
Macchanger is used to change the MAC Address of devices. It is bachelor only for Linux.
Information technology comes in Kali Linux by default.
More than: Larn about macchanger or MAC spoofing in Windows 10 & Linux
#39 ArpSpoof
arpspoof redirects packets from a target host (or all hosts) on the LAN intended for another host on the LAN past forging ARP replies. This is an extremely effective way of sniffing traffic on a switch
Kernel IP forwarding (or a userland program which accomplishes the same, e.k. fragrouter(8)) must exist turned on ahead of time
Arp spoofing / poisoing attack with ettercap tutorial in Kali Linux
#40 Ettercap – MITM AttacK
Man In The Eye assail is very famous set on performed past hacker. In this attack hacker sit between yous and server, and monitor all the network traffic betwixt you and servers on the internet.
Hacker can see what are you browsing, what text y'all are filling on which website. If you are inbound username and password, it tin be seen. So be careful near this attack.
Ettercap is a comprehensive suite for man in the middle attacks. It features sniffing of live connections, content filtering on the wing and many other interesting tricks. It supports active and passive autopsy of many protocols and includes many features for network and host analysis
kali linux man in the center set on tutorial step by footstep
#41 Wireshark
Wireshark is a shark of network monitoring / capturing each every packet traveling over wire or wireless medium.
Using wireshark is enough for a network administrator / Network security researcher to monitor network activity.
Wireshark is the world'due south foremost and widely-used network protocol analyzer. It lets you come across what'south happening on your network at a microscopic level and is the de facto (and often de jure) standard beyond many commercial and non-profit enterprises, authorities agencies, and educational institutions. Wireshark development thrives thanks to the volunteer contributions of networking experts effectually the globe and is the continuation of a project started by Gerald Combs in 1998
Features:
- Deep inspection of hundreds of protocols, with more existence added all the time
- Live capture and offline analysis
- Standard three-pane bundle browser
- Multi-platform: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and many others
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- The most powerful display filters in the industry
- Rich VoIP assay
- Read/write many unlike capture file formats: tcpdump (libpcap), Pcap NG, Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer® (compressed and uncompressed), Sniffer® Pro, and NetXray®, Network Instruments Observer, NetScreen snoop, Novell LANalyzer, RADCOM WAN/LAN Analyzer, Shomiti/Finisar Surveyor, Tektronix K12xx, Visual Networks Visual UpTime, WildPackets EtherPeek/TokenPeek/AiroPeek, and many others
- Capture files compressed with gzip tin be decompressed on the fly
- Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others (depending on your platform)
- Decryption back up for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Coloring rules can be practical to the packet listing for quick, intuitive assay
- Output can be exported to XML, PostScript®, CSV, or plain text
Tutorial for Beginners: Using Wireshark
Download Wireshark: https://world wide web.wireshark.org/#download
Wireshark Tutorial: Wiki
#42 Burp Suite Community
Burp Suite is the leading software for web security testing…
Thousands of organizations use Burp Suite to discover security exposures before it's too belatedly. Past using cutting-edge scanning technology, yous can identify the very latest vulnerabilities. Our researchers frequently uncover make new vulnerability classes that Burp is the first to report
Burp Suite constantly raises the bar of what security testing is able to reach.
Download Burpsuite Community edition : Download Hither
Tutorial of Burp Suite: Web Security
#43 Owasp ZAP Prox
The OWASP Zed Attack Proxy (ZAP) is one of the world's most popular gratis security tools and is actively maintained by hundreds of international volunteers*. It tin can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications. Its also a corking tool for experienced pentesters to use for manual security testing.
Official Website Owasp ZAP
#44 Dardis – Study Writing
When you are working as a Penetration tester/ Ethical hacker / Security Researcher then Yous must submit report to the organization about problems or vulnerabilities.
So yous must know to to write study and transport to organization.
It comes with kali linux by default if you are non user of Kali Linux and so you can download from Hither
Source: https://www.cyberpratibha.com/blog/free-hacking-tools/
Posted by: martinezsweeng.blogspot.com


0 Response to "How Can I Repair A Hacker Lockout On Hp Laptop"
Post a Comment